
Exploring the relationship between storage and security
01 March 2024
Any mission-critical business or entity needs a clear guide to evaluating storage solutions that are optimised to perform for the intended need/use case, and the internal, external, intentional, and unintentional threats the system may face.
By Dr. Doug Milburn, co-founder and president, 45Drives
One of the most common types of data security threats is cyber-attacks, which are malicious attempts to compromise or damage a computer system, network, or data. Cyber-attacks can take various forms, such as malware, ransomware, phishing, and denial-of-service (DDoS) attacks.
In fact, 43 percent of cyberattacks specifically target small businesses. In 2022, 800,944 cyber-crimes were reported in the US, with financial losses rising nearly 50 percent, from US$6.9 to US$10.3 billion. Data breaches, leaks, and exposure affected over 422 million individuals in the US in 2022.
However, not all data security threats are from external attacks. Many threats are from improper access control, which is the application of constraints on who or what is authorised to perform actions or access resources, usually internal to an organisation. Improper access control can result from human error, such as misconfiguration, weak passwords, or lack of awareness. It can also result from design flaws, such as violation of the principle of least privilege, insecure direct object references, or broken authentication.
To prevent data security threats, both from attacks and from improper access control, organisations and individuals should follow a set of best practices and review them frequently to ensure compliance.
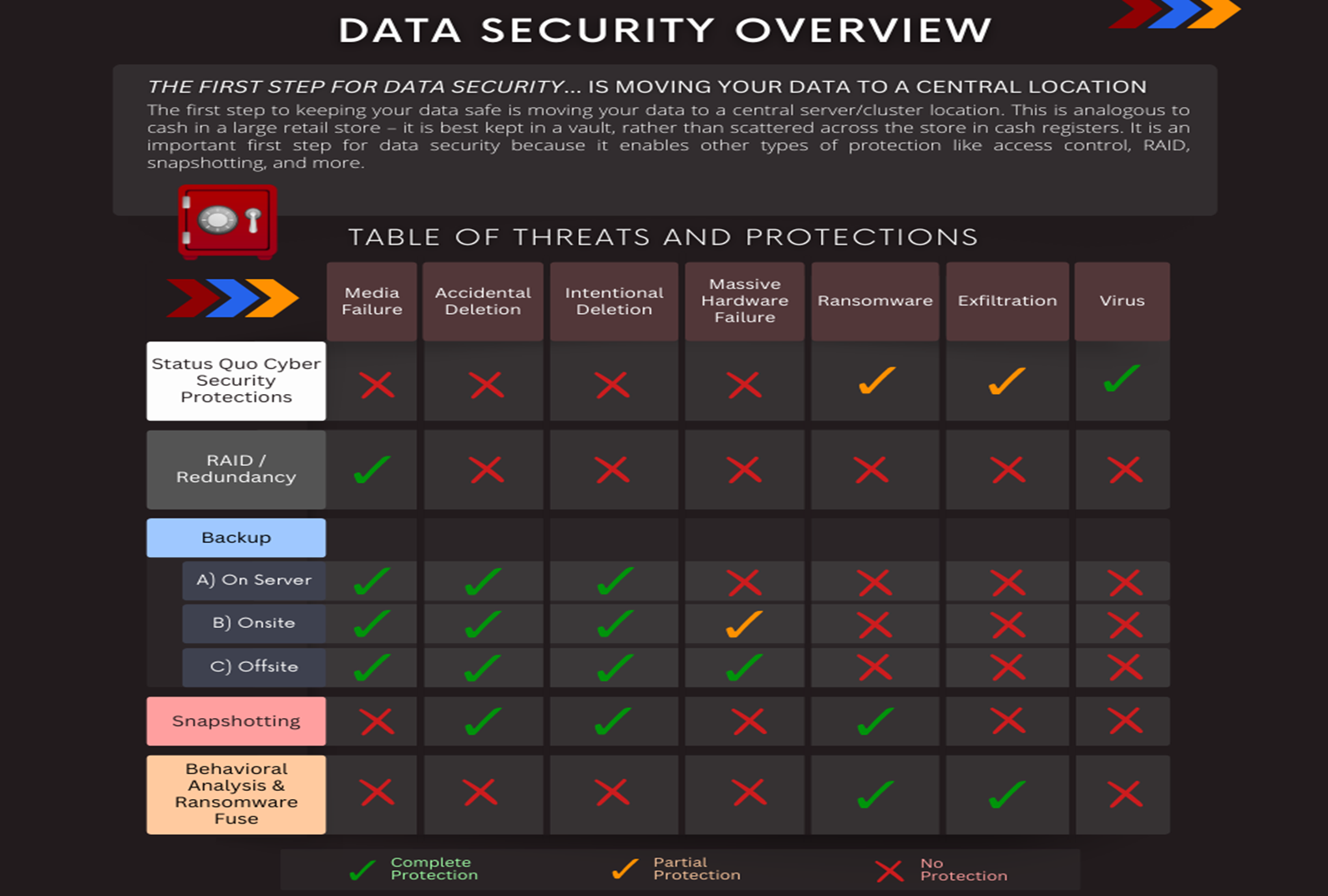
Key Layers of Protection include:
Status Quo Cyber Security Protections: Your status quo cyber security protections include firewalling, access control, and network monitoring.
RAID/ Redundancy: Redundant arrays of independent disks (RAID) offer protection from drive failures. RAID functions by creating redundant chunks of data (parity) that are spread out with your regular data across multiple drives. That parity information can be used to rebuild data if a drive fails. Another type of RAID functions by keeping complete additional copies of your data spread across your drives. RAID is an important layer of protection against media failure, but will not protect you if something catastrophic happens, like a fire or flood. Erasure coding is similar to RAID and is used when clustering. Erasure coding can protect entire servers from failure.
Backup: A backup is a copy of your data. You can use backups to restore your data if you lose your primary copy. Backups protect from bigger threats that could lead to data loss if RAID was your only protection. The 3-2-1 backup rule works as an absolute minimum for backup strategy, wherein you store at least 3 copies of your data, 2 local but on different media, and 1 copy offsite.
On-Server: The lightest form of backups. These allow the quickest restoration, but offer the least protection. Anything that physically affects the server places on-server backups at risk. On server backups exist on the same server as the primary copy of your data.
On-site: Onsite backups are useful for still providing fast and convenient restoration while protecting from more threats than on-server backups. They are vulnerable to catastrophic failures like fire, flood, or meteorite strikes. Onsite backups exist in the same location as your primary copy of data, but on a separate medium.
Off-site: Off-site backups are the most secure and are an essential part of any data security plan. The main considerations that lead to useful offsite backups are how frequently you are backing your data up and how long it will take to restore from the backup. Off-site backups exist in a completely separate location from your primary copy of data.
Snapshotting: Snapshotting allows you to save how the filesystem looked at a certain time so that you can roll back specific files or even the entire system. Snapshotting only takes up space when files are deleted, as it holds onto the deleted blocks. Snapshots can be scheduled to take place and be deleted automatically at predetermined intervals. Depending on your use case and with a proper schedule, snapshots can provide the ability to quickly roll back files with very little data loss and with little overhead.
Behavioural Analysis & Ransomware Fuse: Behavioural analysis software monitors network traffic for ransomware behaviour. If it is detected, the ransomware fuse pops the connection to the client within seconds, stopping the ransomware attack from encrypting your files. Then, the web interface allows you to roll back specifically the few files that were infected.
Brought to you by:












